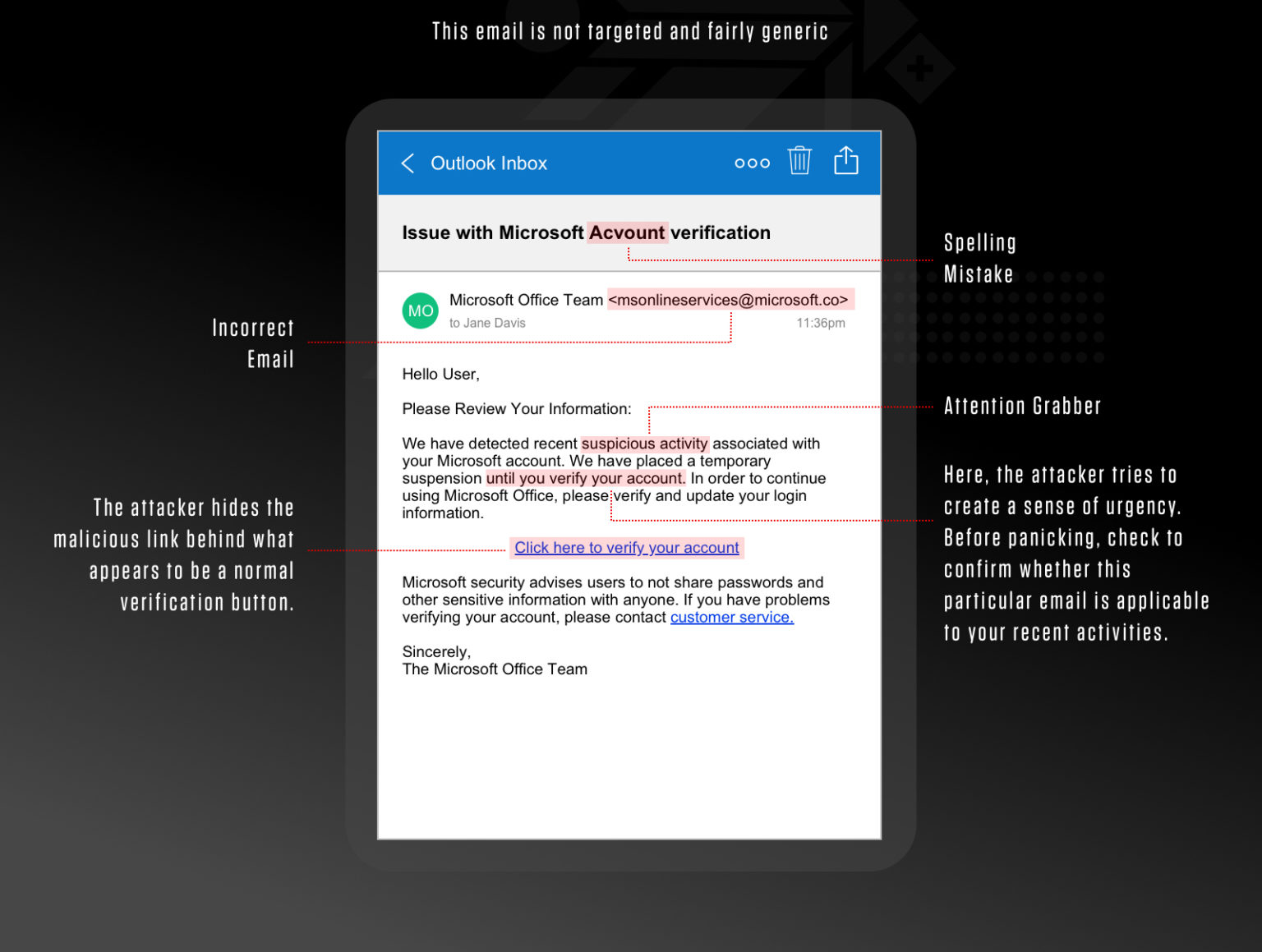
What is email spoofing?
Email spoofing is the act of sending emails with a forged sender address. It tricks the recipient into thinking that someone they know or trust sent them the email. Usually, it’s a tool of a phishing attack, designed to take over your online accounts, send malware, or steal funds.
Spoofed email messages are easy to make and easy to detect. However, more malicious and targeted varieties can cause significant problems and pose a huge security threat.
Reasons for email spoofing
The reasons for email spoofing are quite straightforward. Usually, the criminal has something malicious in mind, like stealing the private data of a company. Here are the most common reasons behind this malicious activity:
- Phishing. Almost universally, email spoofing is a gateway for phishing. Pretending to be someone the recipient knows is a tactic to get the person to click on malicious links or provide sensitive information.
- Identity theft. Pretending to be someone else can help a criminal gather more data on the victim (e.g. by asking for confidential information from financial or medical institutions).
- Avoiding spam filters. Frequent switching between email addresses can help spammers avoid being blacklisted.
- Anonymity. Sometimes, a fake email address is used to simply hide the sender’s true identity.
Dangers of email spoofing
Email spoofing is incredibly dangerous and damaging because it doesn’t need to compromise any account by bypassing security measures that most email providers now implement by default. It exploits the human factor, especially the fact that no person double-checks the header of every email that they receive. Besides, it’s incredibly easy for attackers and requires almost no technical know-how to do it on a basic level. Not to mention the fact that every mail server can be reconfigured to be identical or almost identical to slip by.
How do hackers spoof your email address?
Email spoofing is possible by forging email syntax in several methods of varying complexity. They also differ in which part of the email the attacker will be forging.
Here’s what variation you could encounter when surfing the web.
Spoofing via display name
Display name spoofing is a type of email spoofing, in which only the email sender’s display name is forged. Somebody can do this by registering a new Gmail account with the same name as the contact you want to impersonate. Mind you, the mailto: will display a different email address. If you’ve ever received an email from Jeff Bezos asking you to loan some money – you’ve encountered an example of spoofing via display name.
This type of email will also bypass all spoofing security countermeasures. It won’t get filtered out as spam, because it’s a legitimate email address. This exploits user interfaces built with ease of use in mind – most modern email client apps don’t show metadata. Hence, display name spoofing is very effective due to the prevalence of smartphone email apps. Often, they only have space for a display name.
IndicHosts.net recommends that organization adopts a policy to do-away with email’s display-name altogether, company wide.
Spoofing via legitimate domains
Suppose the attacker is aiming at higher believability. In that case, he may also use a trusted email address in the From header, such as “Customer Support Specialist” . This means both the display name and email address will show misleading information.
This attack doesn’t need to hijack the account or penetrate the targeted company’s internal network. It only uses compromised Simple Mail Transfer Protocol (SMTP) servers that permit connections without authentication and allow you to manually specify the “To” and “From” addresses. Using shodan.io, we can identify 6,000,000 SMTP servers, many of which are guaranteed to be vulnerable. Besides, the attacker can always set up a malicious SMTP server himself.
The situation is dire because many enterprise email domains aren’t using any countermeasures for verification. Still, there are some techniques that you could use to protect your domain – more on that later.
Spoofing via lookalike domains
Suppose a domain is protected, and domain spoofing isn’t possible. In that case, the attacker is most likely going to set up a lookalike domain. In this type of attack, the fraudster registers and uses a domain that is similar to the impersonated domain, e.g.”@doma1n.co” instead of”@domain.co”. This change could be minimal enough not to be noticed by an inattentive reader. It’s effective because when exactly was the last time you bothered to read an email header?
Using a very similar domain, which also bypasses spam checks due to being a legitimate mailbox, the attacker creates a sense of authority. It might be just enough to convince its victim to reveal their password, transfer money, or send some files. In all cases, email metadata investigation is the only way to confirm whether the message is genuine. However, it’s sometimes plain impossible to do on the go, especially with smaller smartphone screens.
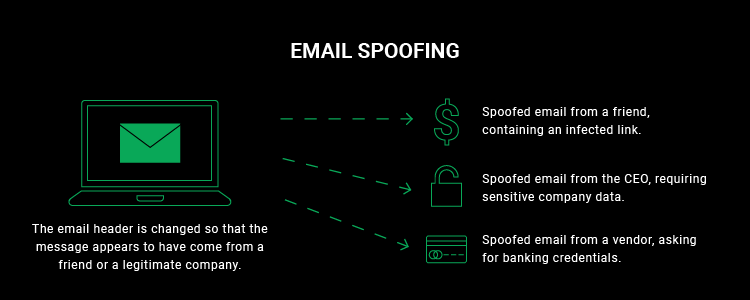
How to stop email spoofing?
Emails are the lifelines of most businesses, but they’re also popular targets for cyberattackers. Business Email Compromise (BEC) and email spoofing are two terms you might hear often in cyber threat briefings. These tactics are getting smarter and more deceptive, but don’t worry – there are clear steps to protect your inbox.
1. Authenticate Your Emails:
- SPF, DKIM, and DMARC: Think of these as your email’s ID cards. They help confirm the email is coming from who it says it’s coming from. This can we enabled through your web hosting control panel or make a ticket for us to do it for you.
2. Knowledge is Powner:
- Recognize the Red Flags: Be wary of unexpected emails, and hover over links to see their true destination.
- Double-Check Email Addresses: Even if an email’s name looks right, the actual address might give away a scam.

3. Upgrade Your Email Defenses:
- Invest in stronger email security. Some tools can analyze threats and even “sandbox” suspicious items to check them in a safe space.
- IndicHosts offers premium email filtering by SpamExperts to assist with your email defence strategy.
4. Two Steps are Better Than One: Multi-Factor Authentication (MFA) adds an extra layer of security. Even if someone knows your password, they won’t get very far without the second verification step. Upcoming version of cPanel now implements MFA for IndicHosts web hosting‘s webmail interface.
5. Back it Up: Regularly save important data. If a cyber attacker holds it hostage, you can bounce back without paying them off.
6. Communication Policies:
- Verify Big Requests: If someone asks for sensitive info or money, double-check with them through another method, like a phone call.
- Spot External Emails: Some businesses mark outside emails with tags like “[EXTERNAL]” to make them stand out.
7. If It Looks Fishy, Report It: Encourage your colleagues to speak up about strange emails. Everyone staying alert makes it harder for scammers to succeed.
8. Filter Content: Just like a coffee filter catches unwanted bits, content filters in your email system can weed out harmful content.
9. Stay Updated: Just as you’d update your smartphone, regularly updating and patching your email software keeps it secure against known threats.
10. Keep a Low Profile: Try not to splash individual email addresses all over the web. Instead, use general ones like “[email protected].”
11. Be Selective: Consider creating an email VIP list (whitelist) or a no-entry list (blacklist) to manage who can reach your inbox.
In conclusion, while technology can bolster our email defenses, the real power lies in being informed and vigilant. Regular training and a sharp eye can be your best shields against email threats. Stay safe and always be email-smart!