Looking to secure your WordPress website? Protect it from potential XML-RPC exploits with our expert tips and guidance. Our comprehensive tutorial will walk you through the necessary steps to prevent this common vulnerability, ensuring the safety and integrity of your site. Stay one step ahead of hackers and fortify your WordPress security today.
About XML-RPC
XML-RPC is a protocol for remote procedure calls which uses XML for the data exchange. In XML-RPC the client that wants to make a call to a remote method creates the input parameters in the form of XML and sends it via an HTTP request to a remote server implementing the XML-RPC protocol.
Understanding XML-RPC in WordPress
WordPress is a complete blogging platform. It is made highly customizable and easy to develop the website. Using WordPress XML-RPC can create WordPress blogging clients, some other software which does some batch tasks like creating multiple posts from a file, etc. The XML-RPC system can be extended by the WordPress plugins to modify its behaviour. The XML-RPC functionality is turned on by default since WP 3.5. XML-RPC turned on by default – especially with the mobile devices and third-party desktop apps that use it to communicate with WordPress.
The issue with XMLRPC is that it can cause CPU and memory exhaustion and the site’s database to reach the maximum number of open connections. That will cause the vulnerable site (and server) to go down for a period of time, hence affecting Availability of your website.
There are four ways that WP‘s XML-RPC API could be abused by an attacker:
- Intel gathering — attacker may probe for specific ports in the target’s internal network
- Port scanning — attacker may port-scan hosts in the internal network
- DoS attacks —Apart from the data transfer, xmplrpc.php is also responsible for enabling the pingbacks and trackbacks. These are the notifications that you receive when a blog or a third-party website links to your website. Although it has been replaced, some websites still use XML-RPC.php for backward compatibility. If you are one of them, hackers can launch DDoS attacks on xmlrpc.php by sending a large number of pingbacks and put your site out of action or you can say – make it unavailable for your users.
- Router hacking — attacker may reconfigure an internal router on the network
- Brute-force attacks – XML-RPC (XML-remote processing call) allows encoded remote calls transported via HTTP that enables you to remotely post, edit, or delete a file or content from your WordPress website. With each request, xmplrpc.php sends the authentication information. It makes it easier to push a large amount of data at one time. But the ability to push a large amount of data at one time implies that even hackers can also sneak-in a number of passwords to it. If a hacker sends enough authentication requests with a different combination of username and password, they might get it right eventually, and as in result, your site gets compromised.
Check if XML-RPC is already disabled on your blog
Before we go any further we need to do a simple check to validate of XML-RPC is enabled on your blog. To test that try accessing the xmlrpc.php file in your browser by access the URL https://domain.com/xmlrpc.php (replace domain.com with your domain name).
If it is disabled, you’ll get a “403 – Forbidden message”. If you get any other message, read further to understand your mitigation options.
Code based mitigations or workarounds
1. If you aren’t using the XML-RPC functionality for anything, to protect against any vulnerabilities, add below lines .htaccess:
# protect xmlrpc <IfModule mod_alias.c> RedirectMatch 403 /xmlrpc.php </IfModule>
2. To redirect requests for xmlrpc.php to a custom page, modify the RedirectMatch like so:
# protect xmlrpc Redirect 301 /xmlrpc.php http://example.com/custom-page.php
3. Denying all access to xmlrpc.php:
# protect xmlrpc <Files xmlrpc.php> Order Deny,Allow Deny from all </Files>
4. Allow access to xmlrpc.php for specific IP addresses only.
# protect xmlrpc <Files xmlrpc.php> Order Deny,Allow Deny from all Allow from <IP> Allow from <IP> </Files>
You can also add following code to your wp_config.php after the line require_once(ABSPATH . ‘wp-settings.php’); if you want to disable XML-RPC for your site.
add_filter('xmlrpc_enabled', '__return_false');
Plugin based mitigation
Disable XML-RPC via a plugin
Simply install and activate the Disable XML-RPC-API plugin. Login to your WordPress backend, navigate to Plugins>>Add New and upload the plugin file. Once uploaded, activate the plugin. It’ll reflect on the left bottom of your WP dashboard.
The plugin works out of the box and will immediately deactivate XML-RPC.
You can navigate to XML-RPC Security » XML-RPC Settings to configure the plugin. For example, you can allow certain users to access XML-RPC by whitelisting their IP addresses.
Validate if WordPress XML-RPC.php is disabled?
Use the XML-RPC Validator to check if XML-RPC is disabled on your WordPress blog.
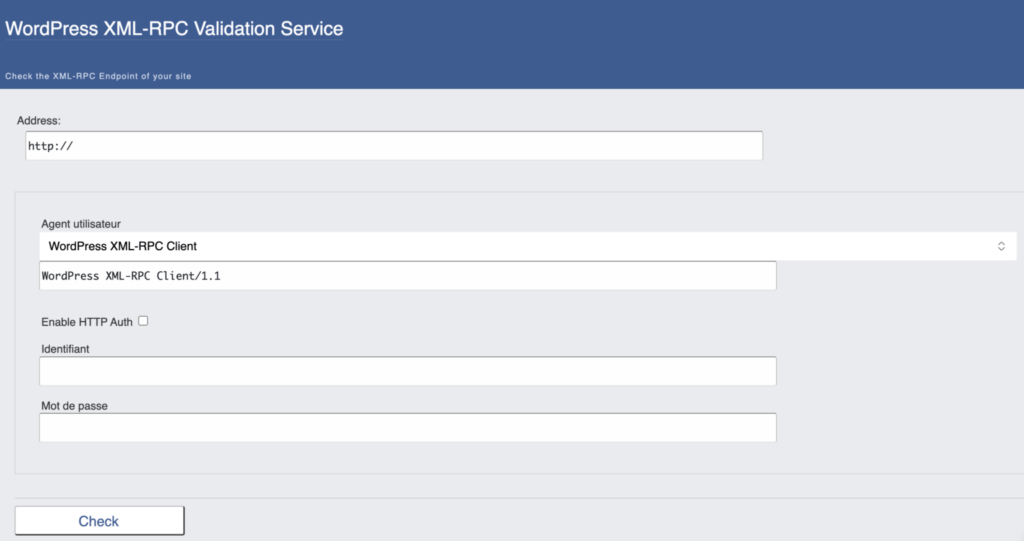
Here are the steps;
- Enter your site’s URL into the text box provided on the XML-RPC Validator page.
- Click the “Check” button to run the validation.
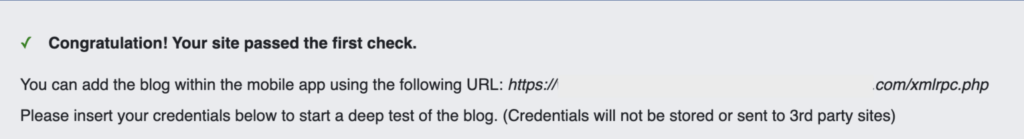
- If XML-RPC is enabled on your site, you will see a message that says “Congratulation! Your site passed the first check.” This means that XML-RPC is enabled and can be accessed.

- If XML-RPC is disabled on your site, you will see an error message instead.